
Zero Trust Network Access : Accès distant nouvelle génération ?
Le Zero-Trust Network Access propose une vision nouvelle de l'accès distant au réseau d'entreprise.

CEO @ Chimere
Get our white paperZTNA: Designing and implementing modern remote access
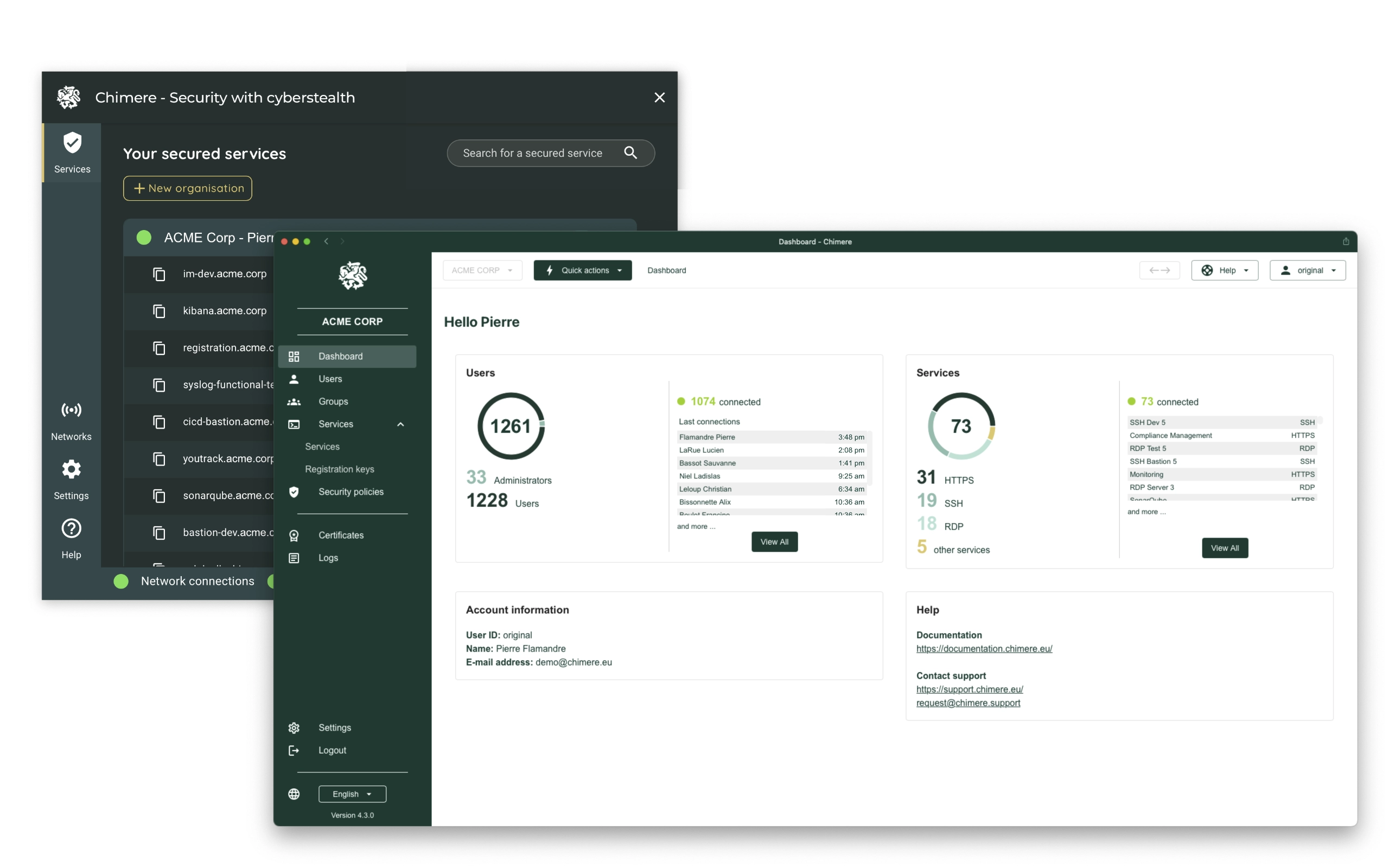
Get it nowChimere is a next-generation remote access solution based on Zero Trust Network Access that provides secure and private access to your applications and services.











ZTNA
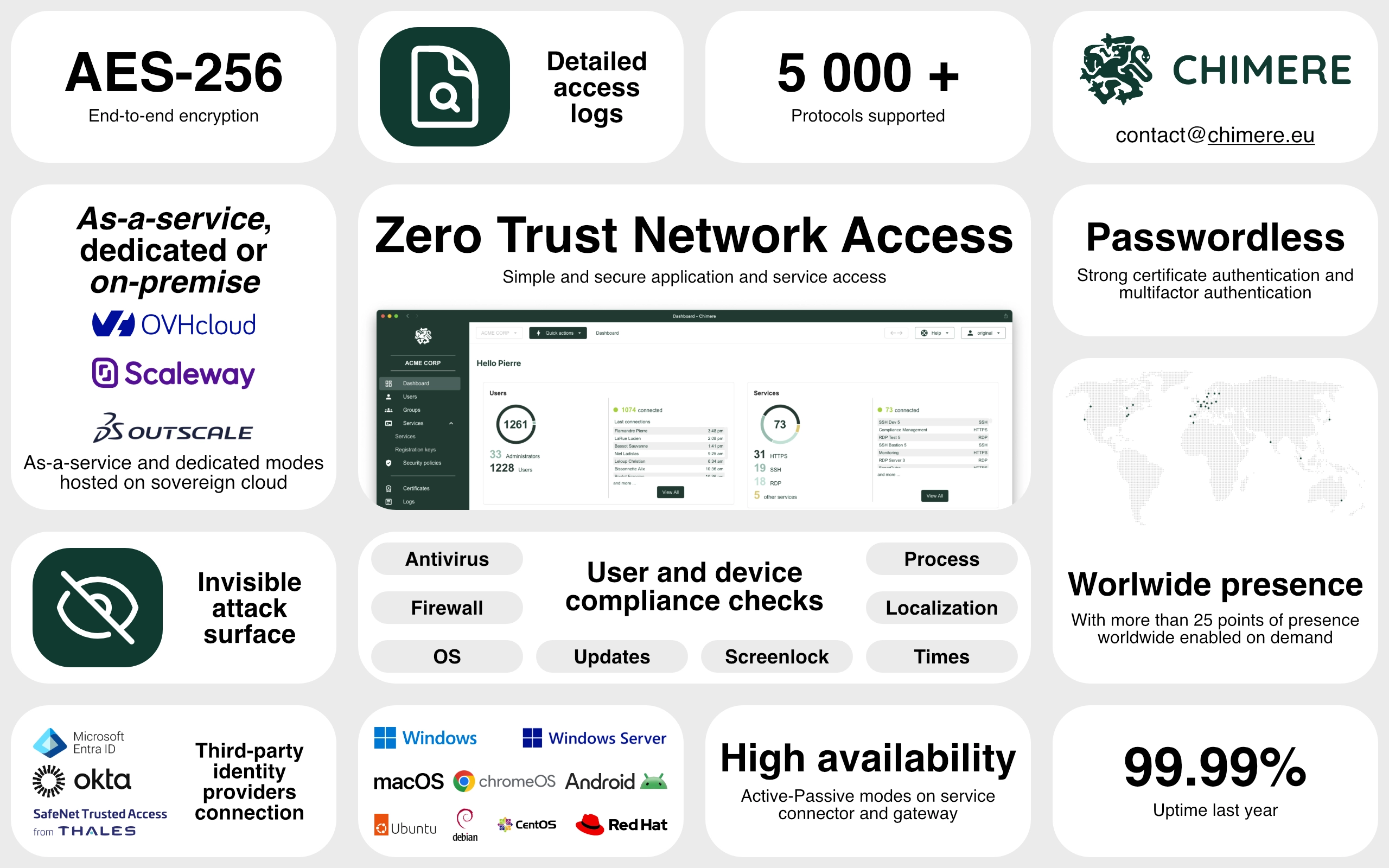
Simplify your network access
Legacy infrastructure are complex and difficult to manage. Chimere simplifies your network access by providing a modern, secure, and easy-to-use solution without single points of failure.

Chimere is hosted on sovereign cloud providers, ensuring data sovereignty and compliance with local regulations. We prioritize security and privacy by partnering with trusted providers like OVHcloud, Scaleway, and Outscale.



Over 25 points of presence worldwide
Leverage a mesh network with more than 25 activable points of presence around the globe to optimize performance and stay as close as possible to your users.
See how Chimere secures remote access, simplifies compliance, and gives you full control, in minutes.

Le Zero-Trust Network Access propose une vision nouvelle de l'accès distant au réseau d'entreprise.

CEO @ Chimere

Two common attack methods to bypass firewall rules and discover services

CTO @ Chimere

What are the prerequisites and where to start for a Zero Trust strategy?

CTO @ Chimere

Meet Chimere at Paris, Espace Champerret on January 28–29, 2026

Meet Chimere in Lille from March 31 to April 2, 2026