The True Zero Trust
Chimere is a European Zero Trust Network Access solution. ![]()

Chimere is a European Zero Trust Network Access solution. ![]()

Zero Trust solution by design
Zero Trust Network Access makes your applications invisible on the internet and within your corporate network. By becoming undetectable, your network services disappear from the list of entry points that attackers can exploit.
Chimere provides native micro-segmentation that prevents any lateral movement, even if your network is compromised. By applying the principle of ZTNA to your enterprise applications, you ensure a point-to-point connection between your employees and their applications, unlike enterprise VPNs where users have access to a part or the entire network.
With just one click, allow all your employees, contractors, and clients to securely access your assets from anywhere in the world. The propagation of access rights or their revocation is immediate and has never been easier.
Zero Trust Network Access offers a new vision for remote access to the corporate network. And with Chimere's ZTNA solution, we invite you to go further and adopt true Zero Trust!
You no longer need to modify your existing network infrastructure, reducing the cost and complexity of migrating to ZTNA. Additionally, this ensures that your team members can continue to access your resources in the same way as before, minimizing disruptions and maintaining productivity.
Don't change your users' habits, Chimere is designed to seamlessly integrate with existing tools, providing a smooth transition to enhanced network security. This approach not only reduces costs and deployment efforts but also minimizes disruptions for end-users.
Our solution seamlessly integrates with existing identity providers, simplifying the user provisioning process. In just one click, administrators can provision new users, assign roles and permissions, and provide secure access to network resources.
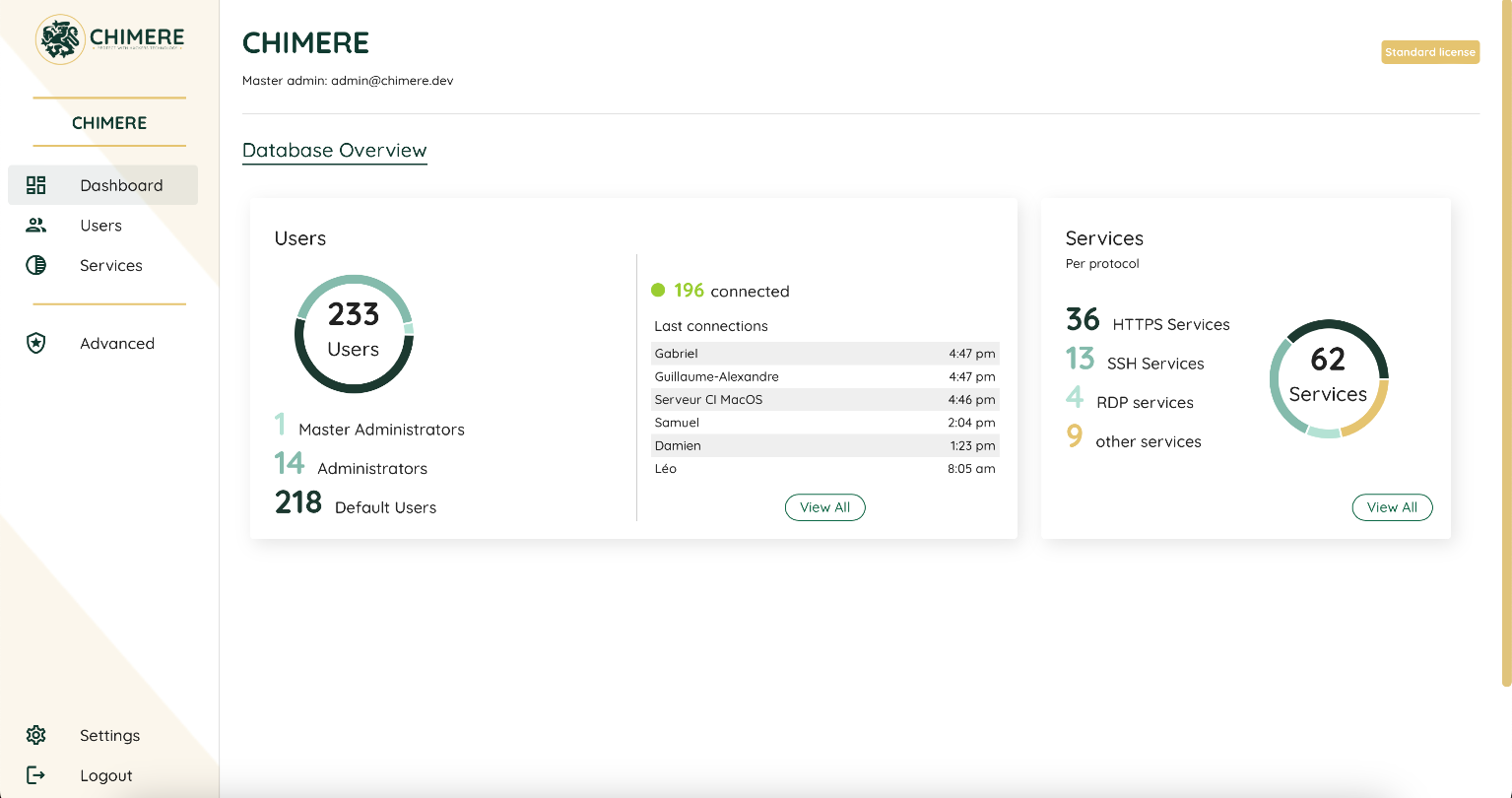
You can precisely track who accesses which applications and services, when, and from where. This also helps you comply with regulatory requirements for tracking and reporting access to sensitive data.
Your employees have access from their mobiles, tablets and workstations to your resources anywhere in the world and without opening your system on the internet network.
Chimere is the safest solution to create secure tunnels to the applications you install within your clients' systems.
Industrial systems or any sensitive application were never made remotely accessible to avoid opening an entry point from the internet. With Chimere, it's now possible.
With Chimere, allow your subcontractors to access the applications they need without providing them with VPN access, and significantly reduce the risk of attack in case of compromise of the companies you work with.
Chimere allows you to stop exposing your VPN gateway. Thus, purely and simply eliminate the associated risk.
The micro-segmentation provided by Chimere allows you to connect to any machine in the fleet from an authorized device, without having to manage multiple hops and openings of flows within the firewalls of each zone.
ZTNA solution in 4 components to bring you the cyberstealth
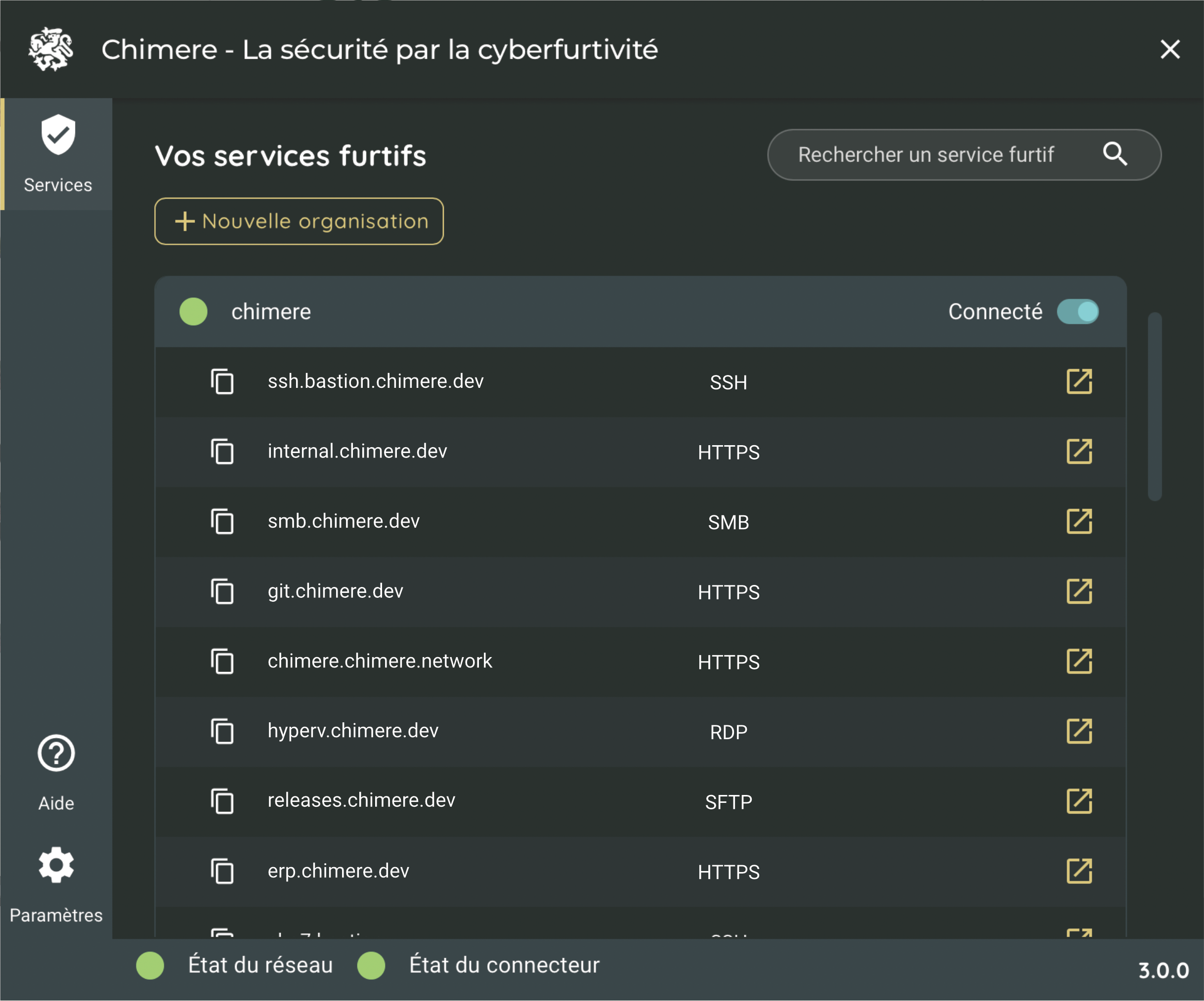
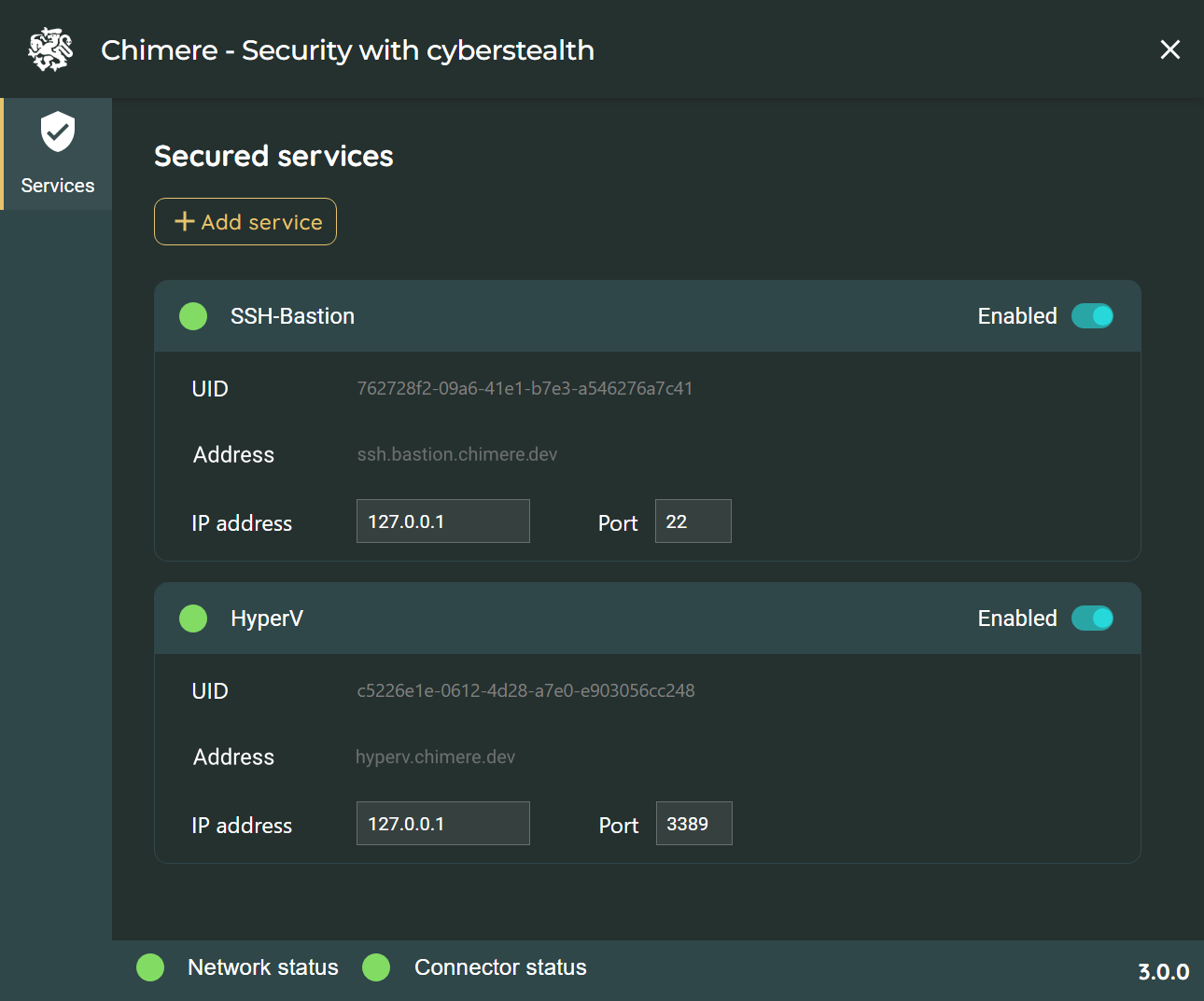
This component allows the user to connect to the ZTNA infrastructure and the applications of their company.
The transfer agent allows the connection and provision of services and applications to users.
The administration console allows managing access rights, users, and secured applications.
The network enables users and protected services to connect without trusting Chimere. The true Zero Trust.


Last news from Chimere's adventure

When securing a corporate network, one naturally thinks of segmentation and organizing network zones by function, application sensitivity, or required level of access. Most of the time, the approach involves isolating these zones by setting up firewalls, blocking traffic, and only opening access as specific requests arise.

Zero Trust addresses multiple contemporary cybersecurity issues with a simple principle: never trust, always verify. There are multiple ways to implement such a concept. But where to start?

The scan had been running for several minutes, and the attacker’s screen displayed a list of listening applications detected on the network. He had entered the post-exploitation phase, meaning he had successfully infiltrated the system and was now trying to extend his control to other devices...







