“ ZTNA improves flexibility, agility and scalability, enabling digital ecosystems to work without exposing services directly to the internet, reducing risks of distributed denial of service attacks.sans exposer les services ”
“Zero trust (ZT) is the term for an evolving set of cybersecurity paradigms that move defenses from static, network- based perimeters to focus on users, assets, and resources. ”


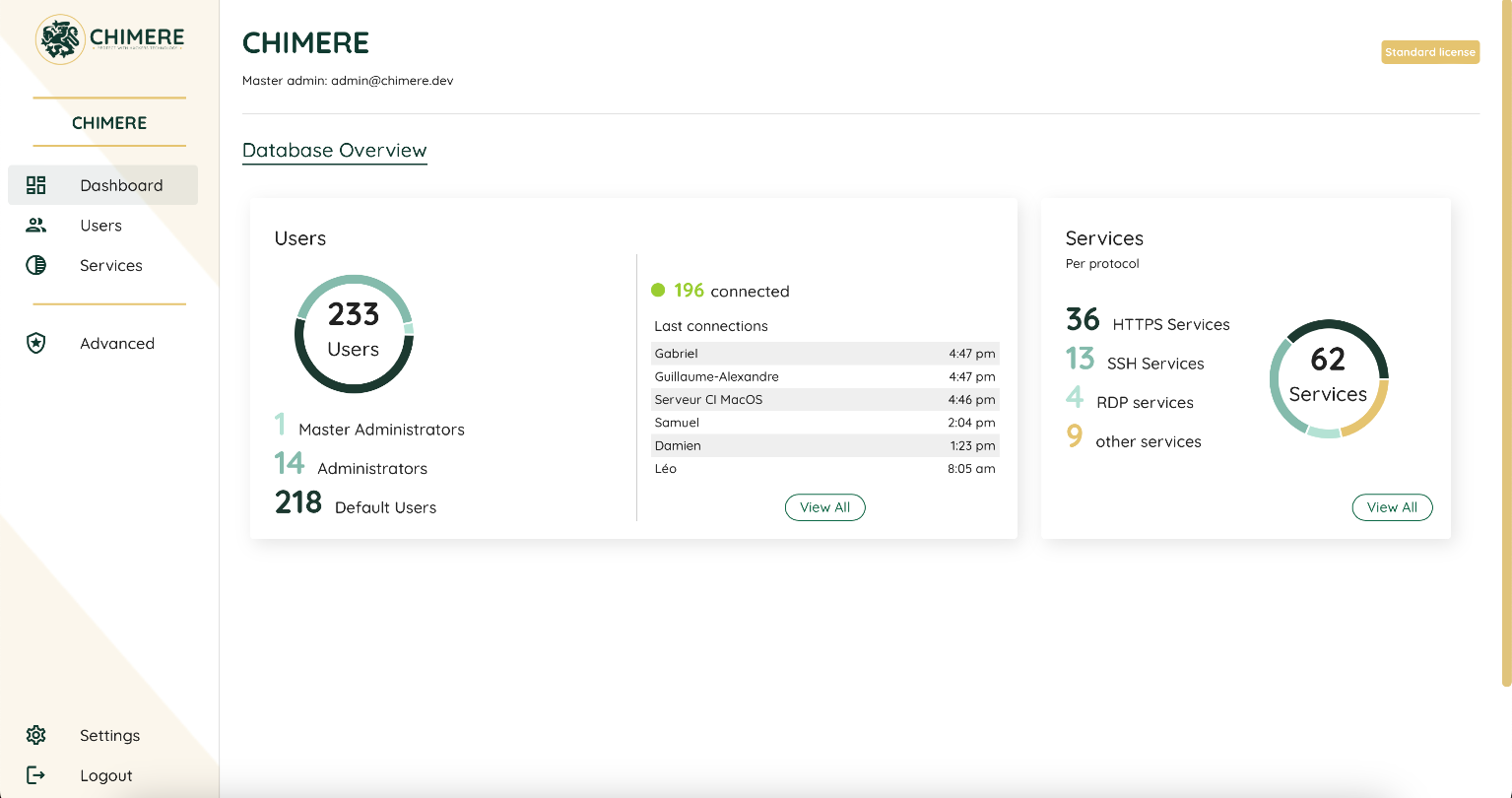

 !
!