Bypassing a local firewall
When securing a corporate network, one naturally thinks of segmentation and organizing network zones by function, application sensitivity, or required level of access.
Most of the time, the approach involves isolating these zones by setting up firewalls, blocking traffic, and only opening access as specific requests arise.
Just like the machines hosting applications, users are also placed in a network zone, sometimes based on the level of trust they are granted. Are they physically present on-site, connected via cable, Wi-Fi? Or perhaps they are working remotely, connected through the company’s VPN?
In the event of an internal threat, whether a malicious employee or if one of the devices or servers is compromised, the firewall's main role is to limit the risk of lateral movements.
What happens if the malicious actor scans the internal network from the machine they control? The firewall blocks unauthorized traffic, and the attacker, in theory, can only discover the services their machine is allowed to contact.
However, a local attacker has tools and methods that allow them to bypass this segmentation in many scenarios.
Here’s an example of an attack that puts into perspective the inherent effectiveness of local firewalls.
The scenario is typical: we have a network zone where the user workstations are located, and other zones where the servers hosting the applications are placed. There is also a central firewall.
Each workstation is configured with a static IP address, allowing network administrators to open traffic flows directly within the firewall.
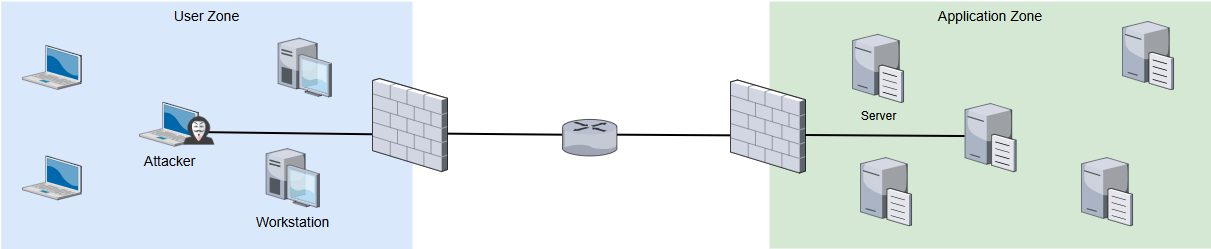
IP address spoofing
Most pentesters are familiar with the adage "Never trust user input".
More specifically, you should never trust input provided by a user by default.
The irony in network security is that the source IP addresses of packets generated by machines are, in a way, user input, and these same IP addresses are the basic element used by firewalls to allow or block traffic.
Based on this principle, an attacker within a network zone, with sufficient privileges on their machine, can:
-
Reconfigure their network card to assign it the IP address of another user’s workstation.
-
Use tools like Scapy to forge IP packets with a spoofed source address, and most importantly, inject such packets into the network.
With a third party’s IP address, the attacker can identify the services that the firewall allows without having to compromise the machine in question, by performing a network scan using Nmap, Masscan, or by developing their own tool based on Scapy.
The attacker may encounter some difficulties: notably managing IP address conflicts within the network zone, which might require waiting for the disconnection of the machine holding the spoofed network card, or pushing the attack further, for instance by using ARP poisoning and tricking devices about the MAC/IP address mapping.
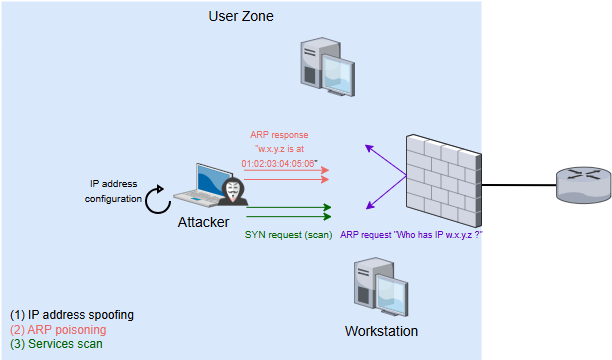
Alternative discovery method: man-in-the-middle
To stay on the theme of ARP attacks, a quieter method involves impersonating the zone’s router and intercepting communications between user workstations and their destinations to generate a rights matrix.
The method combines passive discovery through information gathering with an active attack by poisoning the ARP caches of the workstations and the router. To do this:
-
The attacker generates ARP "is-at" responses, impersonating the router to the user workstations in the zone. They do the same for the router.
-
They enable routing on their machine to relay the received packets, which are not intended for them, and avoid a network denial of service.
-
They monitor packets on their network interfaces with a tool like Wireshark or Tcpdump, recording the source and destination IP addresses as well as application ports. They then log this information in a matrix.
By maintaining this setup long enough, the attacker can gain visibility into access rights, identify applications, the workstations authorized to access them, and perform IP address spoofing in a more targeted manner.
Changing the paradigm and eliminating a category of risks
The two methods presented in this article are classic Layer 2 and Layer 3 OSI attacks.
There are several ways to mitigate them, which require the implementation of additional hardware and software, general hardening, and regular maintenance by network and security experts.
Among the common mitigation methods are:
-
Deploying security probes within the network to detect abnormal packets, block traffic, and raise alerts.
-
Implementing countermeasures such as Dynamic ARP Inspection to specifically combat the family of attacks targeting ARP.
-
Configuring verification mechanisms like Reverse Path Forwarding (which only remain effective if IP spoofing occurs from different network zones).
Moreover, effectively combating attacks on local networks is costly and challenging. A more elegant approach involves changing the communication paradigm between users and applications, or between applications themselves, by using Zero Trust Network Access to:
-
Eliminate the use of IP addresses as a verification element. Instead, base access on the identity of the users themselves, rather than machines or network interfaces.
-
Provide “micro-segmented” access from users to applications, rather than user-to-network access. Avoid relying on network position and configuration to authorize or deny access.
-
Create secure tunnels to applications via the upper layers of the OSI model, such as the application layer (Layer 7), to mitigate risks related to lower-layer attacks targeting application access.
Chimere specializes in this approach, stay tuned for upcoming articles!
