Get our white paperZTNA: Designing and implementing modern remote access
Get it nowFeatures
Continuous posture check
The Zero Trust model emphasizes never trusting and always verifying. Chimere provides a set of rules to check whether the user and the device they are connecting with meet the required standards.
- On-connect and real time detection.
- Allow or deny a user's connection, and also terminate any existing session if the security policy is not met, thanks to real-time verification of device posture and user context.
- From user to organization.
- Apply the right security policies exactly where they matter most — per user, per service, or across your entire organization.
- Fine-grained rules and options.
- Do you want to block? Or just alert? Apply different rules on mobile and desktop? With Chimere, implement rules that match your context and security needs.
A panel of rules to match every needs

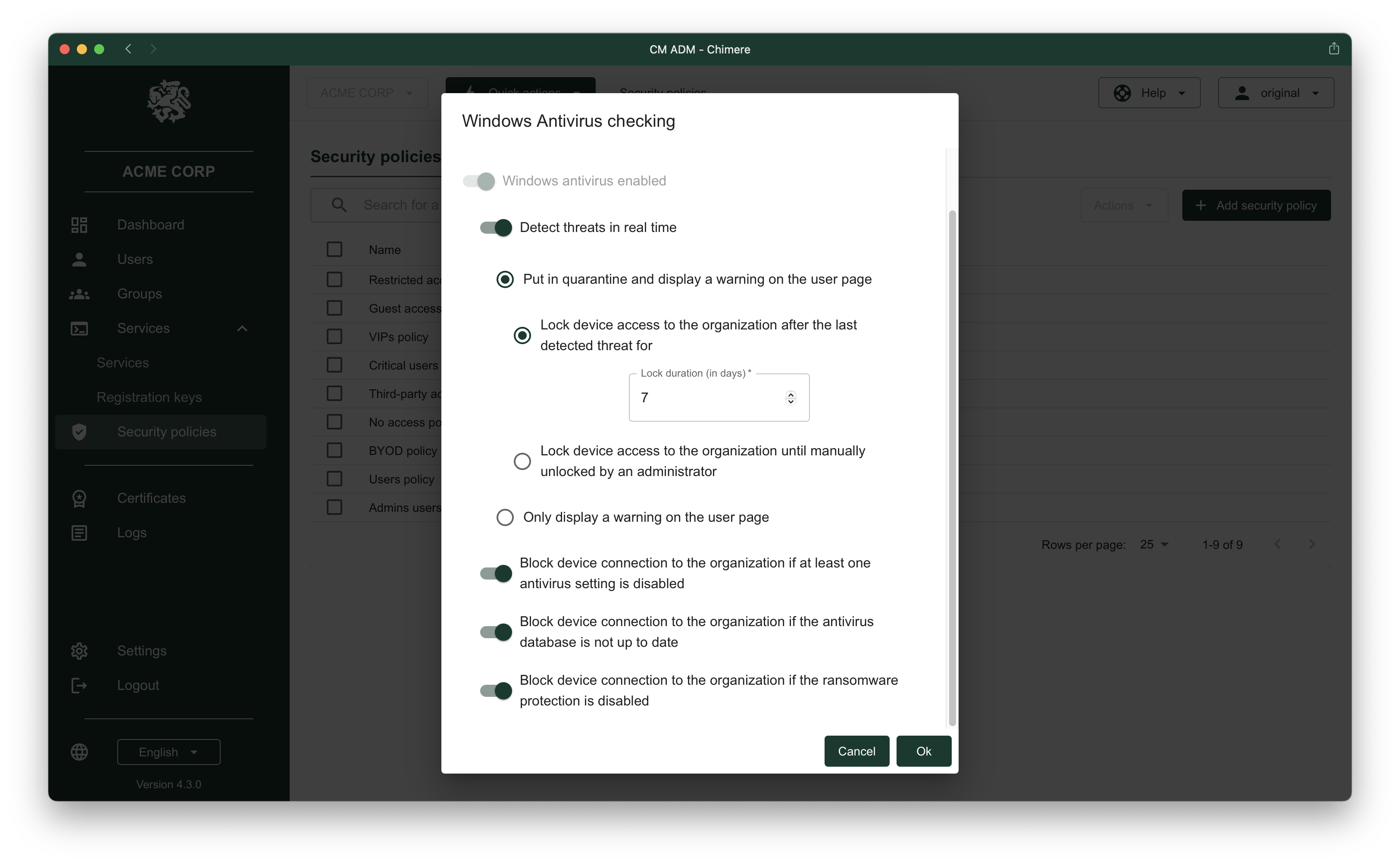
Antivirus compliance
Cut off connections from users when a threat is detected and prevent those with disabled protection from connecting.

Device control
Choose which devices, on which operating systems and versions are allowed to connect to your organization.

Process allow-listing
Available soon
Allow only certain processes on the user's device to access your services.
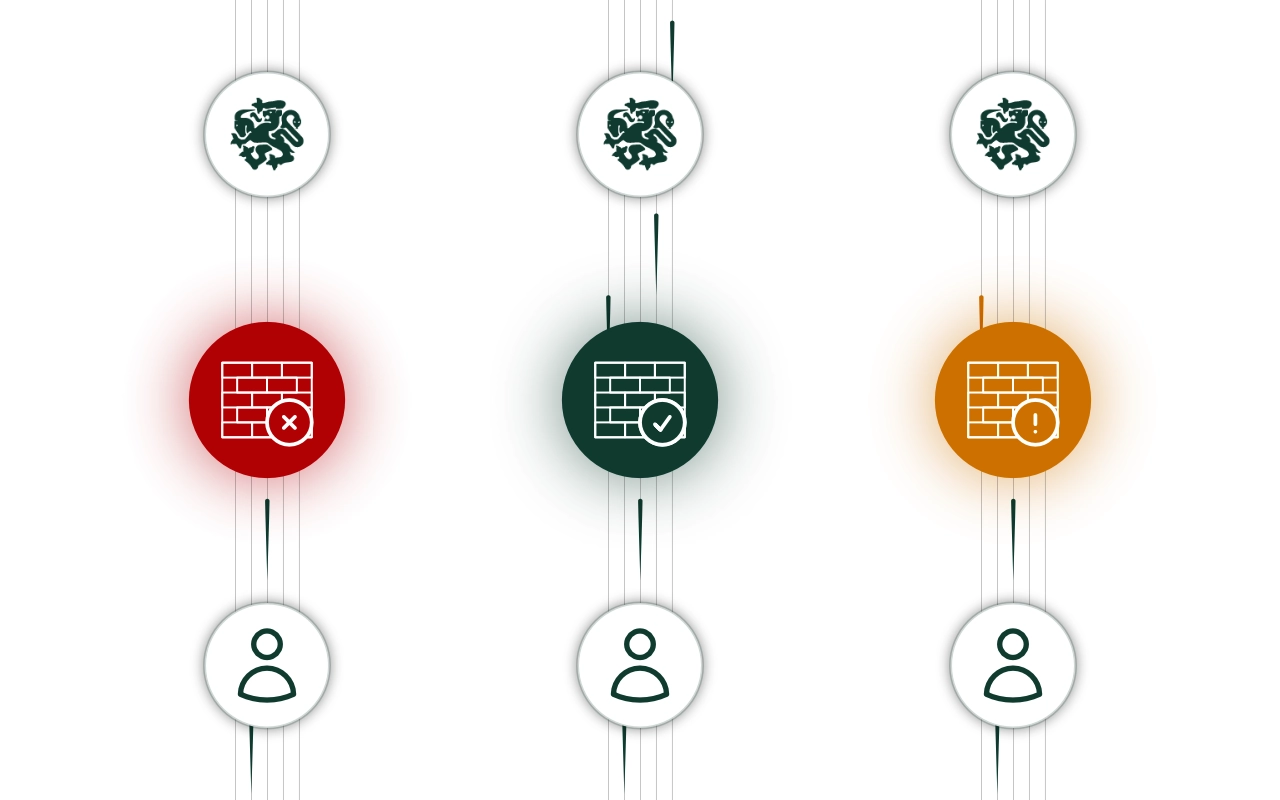
Firewall state
Check the firewall state of users connecting to your services.
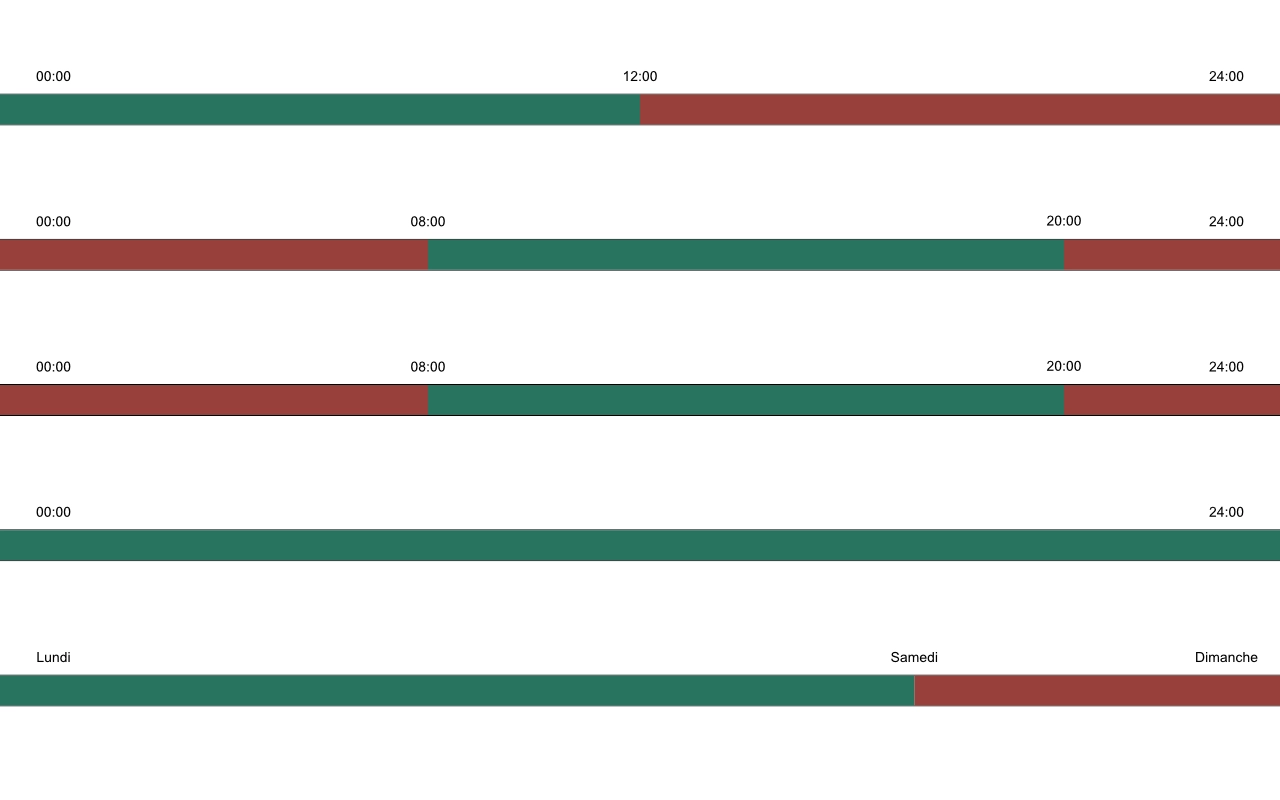
Time check
Available soon
Allow or block connections based on the time of day.

Geolocation check
Allow or block connections based on the user's geolocation.
Discover all features
Chimere combines simplicity, visibility, and power to transform the way your users access your organization’s resources.
- Network access
Zero Trust redefines how users access internal resources. Chimere establishes secure tunnels based on precise access rules, ensuring that each user can access only the services they are explicitly authorized to.
- Passwordless authentication
Eliminate credential theft risks by combining passwordless login with multi-factor authentication (MFA). Chimere integrates with your identity provider to enforce secure and frictionless access.
- Continuous posture check
The Zero Trust model emphasizes never trusting and always verifying. Chimere provides a set of rules to check whether the user and the device they are connecting with meet the required standards.
- Centralized management
Chimere offers a unified interface to manage users, access policies, compliance rules, and audit logs, simplifying administration across your entire infrastructure.
- Detailed logging
All user and service activity is logged in detail, giving your security teams the insight they need for audits, forensic analysis, and real-time monitoring.
- Invisible attack surface
Chimere eliminates the concept of a publicly reachable network. All traffic is initiated outbound by the agent, removing the need to expose any service to the internet, drastically reducing your attack surface.
Ready to dive in?
Start your free trial today.
See how Chimere secures remote access, simplifies compliance, and gives you full control, in minutes.