Get our white paperZTNA: Designing and implementing modern remote access
Get it nowFeatures
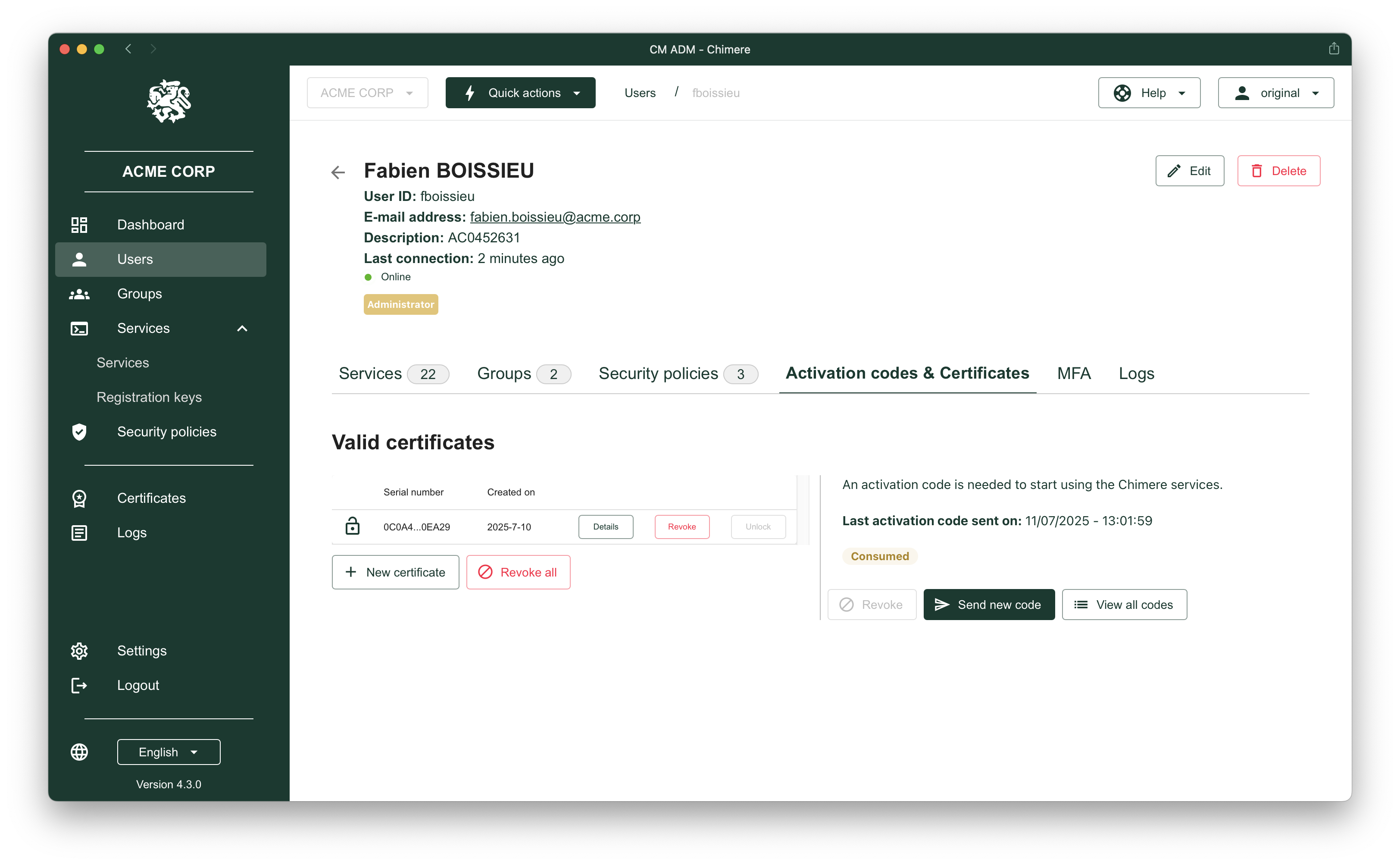
Passwordless authentication
Eliminate credential theft risks by combining passwordless login with multi-factor authentication (MFA). Chimere integrates with your identity provider to enforce secure and frictionless access.
- No passwords, no phishing.
- By removing passwords from the equation, Chimere eliminates one of the main attack vectors. Users authenticate using certificates, phishing-resistant by default.
- Built-in MFA.
- Multi-factor authentication is natively integrated, combining device-bound credentials with OTP validation.
- Federated identity support.
- Chimere integrates seamlessly with your existing identity providers (IdPs), enabling SSO and centralized access management.
Discover all features
Chimere combines simplicity, visibility, and power to transform the way your users access your organization’s resources.
- Network access
Zero Trust redefines how users access internal resources. Chimere establishes secure tunnels based on precise access rules, ensuring that each user can access only the services they are explicitly authorized to.
- Passwordless authentication
Eliminate credential theft risks by combining passwordless login with multi-factor authentication (MFA). Chimere integrates with your identity provider to enforce secure and frictionless access.
- Continuous posture check
The Zero Trust model emphasizes never trusting and always verifying. Chimere provides a set of rules to check whether the user and the device they are connecting with meet the required standards.
- Centralized management
Chimere offers a unified interface to manage users, access policies, compliance rules, and audit logs, simplifying administration across your entire infrastructure.
- Detailed logging
All user and service activity is logged in detail, giving your security teams the insight they need for audits, forensic analysis, and real-time monitoring.
- Invisible attack surface
Chimere eliminates the concept of a publicly reachable network. All traffic is initiated outbound by the agent, removing the need to expose any service to the internet, drastically reducing your attack surface.
Ready to dive in?
Start your free trial today.
See how Chimere secures remote access, simplifies compliance, and gives you full control, in minutes.