Passwords are going to disappear
They are everywhere and have been used since the 1960s. Their invention is often attributed to Fernando Corbató, one of the pioneers of time-sharing operating systems.
Originally, they allowed multiple users to share the same machine by partitioning spaces and protecting their data.
As with modern operating systems, each user was assigned an account with a password.
The most notable difference from recent methods is how storage was handled: passwords were stored in plain text in a file, along with those of all other users of the system.
Some pentesters and developers will admit that this method is still not entirely outdated for many contemporary software developers.
Passwords have always existed. Why will they disappear in the coming years?

Making life impossible for users
IT professionals reading this article, you know exactly what I'm talking about.
No matter your job, and even if you're not directly the IT point person at work, you're probably the tech expert within your family.
One of your weekend missions is helping your relatives reconnect the living room printer to the home network or… recovering a lost Facebook account.
In these tasks, you inevitably deal with password management, trying your best to enforce basic hygiene rules: a different password for each service, its complexity, or regular rotation (which never actually happens).
In the end, passwords are handed over to a dedicated password manager. Eventually, we end up managing the manager itself, theoretically simplifying life and applying security rules that become obsolete all too quickly.

A pain for developers too
Plain-text password storage quickly showed its limitations when database leaks became commonplace.
The first countermeasures involved applying hashing techniques, with algorithms evolving rapidly over the years.
Their successive obsolescence forced defenders to continually reevaluate the hashing methods used, inevitably leaving some outdated protection systems in place.
From DES-based to MD5, SHA-1, and more recently, recommended methods like bcrypt, scrypt, PBKDF2, and Argon2, combined with the use of salts and peppers to complicate recovery attempts from the hash.
Storing passwords securely is a complex task, and the state of the art in this area evolves too frequently.

The failure of current multi-factor authentication
As if password management wasn't already complex enough, a new concept was introduced: multi-factor authentication (MFA). Over the years, as attacks became more sophisticated, defenders realized that passwords could be obtained relatively easily, especially through social engineering.
A way had to be found to address situations where an attacker knew the victim's password. So, the solution was to ask users to authenticate in an additional way, such as by proving ownership of a device. Thus, besides proving knowledge of their password, the user had to demonstrate possession of a device, typically by entering a one-time code received via SMS or using a pre-configured authentication app on their smartphone.
This method has failed for two main reasons:
-
The extra authentication step complicates the user experience, creating frustration when security should be transparent and easy to use.
-
It is bypassable in many situations. Often, attacks adapt, and bypass methods for MFA have not only appeared but have become industrialized through tools like Evilginx2, Modlishka, or Muraena. Targeted attacks by motivated hackers also employ techniques like SIM swapping or continue to use social engineering methods like MFA fatigue or vishing.
Let’s agree, MFA significantly reduces the risk of account compromise, but at what cost?
Are there not more elegant, less cumbersome, and more effective methods?
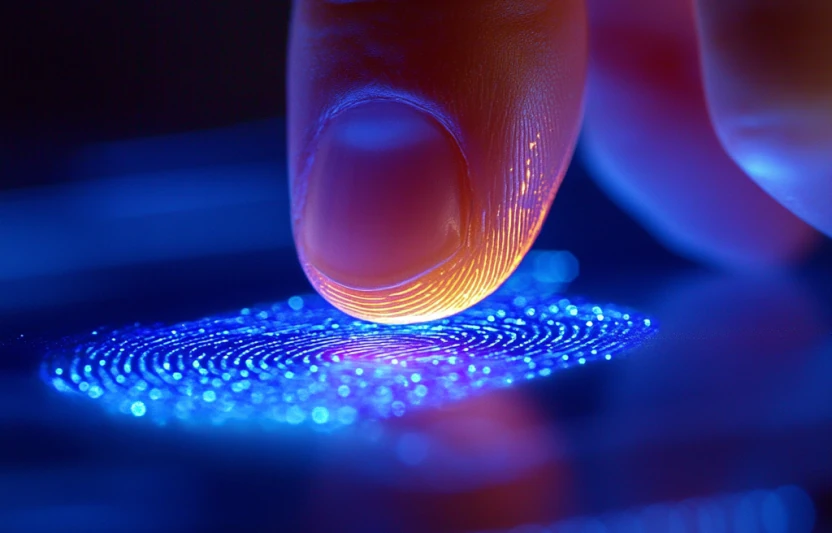
FIDO2: the "Passwordless" and Zero Trust solution
In 2018, the FIDO (Fast Identity Online) alliance introduced a set of specifications known as FIDO2. The idea is to eliminate the need for passwords while incorporating strong authentication and multi-factor mechanisms through known and robust cryptographic methods. When registering for a service, an authentication device (such as a USB key, smartphone, or biometric sensor) generates a pair of keys, with the public part transmitted and stored by the service.
The device, meanwhile, retains the private key associated with the service’s identity (such as a URL for a web service), protecting it with symmetric encryption. The key is, for example, derived from the user’s fingerprint.
During authentication, the server informs the browser that FIDO2 authentication is required via a protocol called WebAuthn and issues a cryptographic challenge. The browser relays this request to the device holding the private key through another protocol: CTAP, implemented by the operating system. The authentication device then solves the challenge using the user's private key, which is unlocked following a biometric authentication request.
This method offers several advantages:
-
The user no longer has to manage passwords, significantly simplifying their life.
-
The security risks inherent in password usage disappear. The authentication is strong and uses modern methods, particularly through asymmetric cryptography. If the service’s key database is compromised, the attacker only has the users' public keys. Most attacks that could occur due to stolen passwords or their hashes are no longer relevant.
-
Multi-factor authentication still exists but in a different and less cumbersome form. It is more transparent and mainly relies on the possession of the authentication device (what the user has) and the ability to unlock it, for instance, with a fingerprint (what the user is).
This type of mechanism aligns with Zero Trust transformation strategies. Trust is never assumed, always verified, through multiple criteria, whereas initial authentication was based solely on one factor: what the user knows, i.e., their password.
Adoption timeline?
Despite the many advantages of this system, several barriers remain to its widespread adoption. The main ones include:
-
The presence of legacy applications within IT environments that do not implement this type of authentication and still require the traditional use of passwords;
-
The investment in hardware, particularly in authentication devices for all users;
-
The shift that must also be made by application developers to make their software compatible with these authentication methods.
Adoption is gradual, and while current imperfect methods (such as MFA) can be easily criticized, they represent an essential intermediate step. They will pave the way for more reliable, secure, and less cumbersome methods in the future.
