Effectively manage your exposure surface (Part 1)
When you are a CISO or CIO taking on a new position, one of the challenges is to efficiently understand the areas where protection measures and security actions need to be implemented. Esteemed readers of this blog, you know how exposing applications on the internet is one of the most common causes of information system compromise. If this is your first Chimere article, take a look at our previous thoughts on the subject: 10 cyberattacks that exploited the principle of exposure, 3 types of attacks feared by companies, and 3 strategies to protect your information system from internet scans (and resulting attacks)
In this article, we provide a method to identify and manage this exposure, ultimately reducing the risk of compromise resulting from the exposure of your assets on the internet.
Identify your exposure surface
The first step is to identify and catalog all assets that could serve as entry points for attackers. To achieve this, we will use a French External Attack Surface Management (EASM) solution called Uncovery. Leveraging Uncovery allows us to adopt the perspective of an attacker and create a detailed map of assets exposed on the Internet within our system.
One key characteristic of EASM solutions is their "agentless" nature. This means they require no specific deployment within the company's infrastructure and operate externally, similar to how an attacker would.
In general, any EASM solution should be capable of providing the following four essential functionalities:
- Discover assets and classify them in an inventory
- Continuously monitor assets to identify any changes
- Evaluate and prioritize the risk level of assets (misconfigurations, vulnerabilities, shadow IT, etc.)
- Integrate with third-party tools (ticketing, messaging, SIEM) used by operational teams to facilitate remediation.
Uncovery is ideal for meeting these needs: it is a 100% automated SaaS solution that provides high visibility into assets exposed on the Internet through an accurate, up-to-date inventory, without false positives. It also assesses their risk level to guard against cyber threats.
Another advantage of Uncovery is its user-friendliness. The tool only requires minimal information about the environments to scan, such as domain names or IP addresses, to yield valuable results.
We requested the technical teams managing the information system to provide us with the Configuration Management Database (CMDB) document containing all known exposed assets. In this case, we are dealing with a medium-sized information system: the document indicates the existence of 33 domain names and an IP address range in /24.
We input this information into the Uncovery interface and initiate a scan:
 Listing of assets in the Uncovery solution
Listing of assets in the Uncovery solution
After 90 minutes, the results are in, providing valuable information about the types of services:
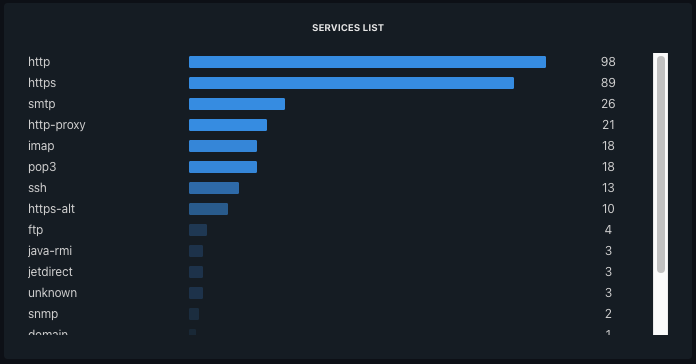 Services identified by Uncovery
Services identified by Uncovery
-
It is noticeable that the majority of exposed services are Web-based (HTTP and HTTPS). In general, these services constitute the vast majority of applications that companies expose. On average, 75% of exposed services are web services.
-
Alongside web services, we find assets whose exposure is absolutely necessary, such as:
- SMTP, which is crucial for relaying external emails to employees' mailboxes.
- Domain (DNS), used to resolve domain names to IP addresses and exposed for use by the company's institutional websites to provide resources to visitors.
-
Additionally, we observe a significant number of exposed services that shouldn't be:
- HTTP proxies used to filter Internet access for company employees. Since these servers are internal and exclusively for employees, they should not be exposed on the Internet, even for remote users.
- POP3 and IMAP mail access points. Similarly, these services serve as entry points to users' mailboxes and ideally should never be exposed.
- System administration, network, and file-sharing services like SSH, SNMP, and FTP.
- Java-RMI services, well-known to attackers and pentesters.
- Print servers.
Taking a broader perspective, the scan helped us identify 32% more assets than listed in the CMDB. We can add this information to the file and, more importantly, take the investigation a step further.
Illegitimate exposed web applications
The scan has identified over 300 exposed services, and among them, we know that 82 should not be exposed as they are exclusively intended for company employees. However, it's also possible that some of the web services identified fall into this category, but the "services list" view of the results is not sufficient to discriminate them.
Uncovery, however, allows us to obtain this information.
The tool takes screenshots of all web applications detected during the scan, with HTTP status code 200. At a glance, we can determine which ones are meant to be accessible from outside, worldwide, and which ones are intended for a restricted population of users. The presence of authentication screens is often a characteristic of private applications not meant to be accessed by just anyone.

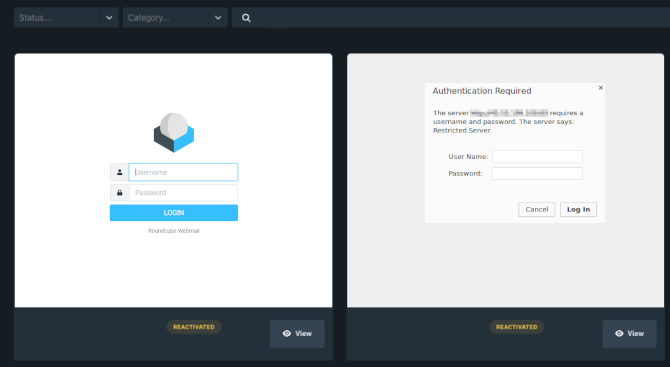 Screenshots automated by Uncovery
Screenshots automated by Uncovery
Here, we observe that among these applications, there are instances of cPanel, webmail RoundCube, VPN authentication screens, and web applications protected by htaccess.
In total, we note that 78 of the web services listed by the tool are business applications, potentially serving as an additional entry point for attackers and should not be exposed either. We now have a solid foundation to work on, to reduce, manage, and secure our exposure surface.
What's next?
We have identified a 30% gap between our internal reference and the actual number of assets visible from the Internet. Additionally, we have pinpointed 160 services exposed on the Internet that should not be.
Now that we have a precise view of the scope, we can address it. In the next article on this blog, we will explore how to use Chimere to make these 160 services invisible and eliminate their exposure while still allowing access for the company's employees and subcontractors. We will delve into automating the registration of these services within the Chimere network, cutting their exposure, and accessing them from user workstations. Furthermore, we will discuss how to verify the proper functioning of the implemented measures.
N’oubliez pas de vous inscrire à la newsletter Chimere pour ne pas manquer les prochains articles:

