How to use the Tor darknet to protect your information system?
In the article about the issue of service exposure and 10 cyber-attacks that have exploited the principle of exposure, we highlighted the risks associated with exposing services on the internet.
But what if we could conceal these services, preventing them from being discovered by just anyone?
One way to achieve this is by using the Chimera network and its hidden services mechanism it offers. However, if you have only a few services and users to manage, performance is not a concern, and you enjoy getting your hands dirty, why not directly use the Tor network? This method is particularly interesting for individuals or small enterprise information systems.
Let's see how to protect an SSH service and avoid becoming a target for attacks. Let's dive in!
The beginning: an exposed SSH service on the internet. And attacked.
For this article, we have a Linux server with an SSH administration service listening on the internet.
Exposing the SSH port is very convenient for remote server administration. However, it also poses a significant security risk. To fully understand the problem, we can analyze the traffic directed towards the service.
For this purpose, we use the TCPDUMP tool, which displays real-time network packets captured by the machine. We configure the tool to only display TCP packets with the SYN flag activated and directed to port 22. In other words, we filter the traffic to only show connection attempts to our SSH service exposed on the internet. We run the following command:
tcpdump -ni ens3 'tcp[tcpflags] == tcp-syn and tcp[tcpflags] != tcp-ack and port 22'
Not surprisingly, as soon as our SSH service becomes available, it is already being targeted by attacks and network scans:
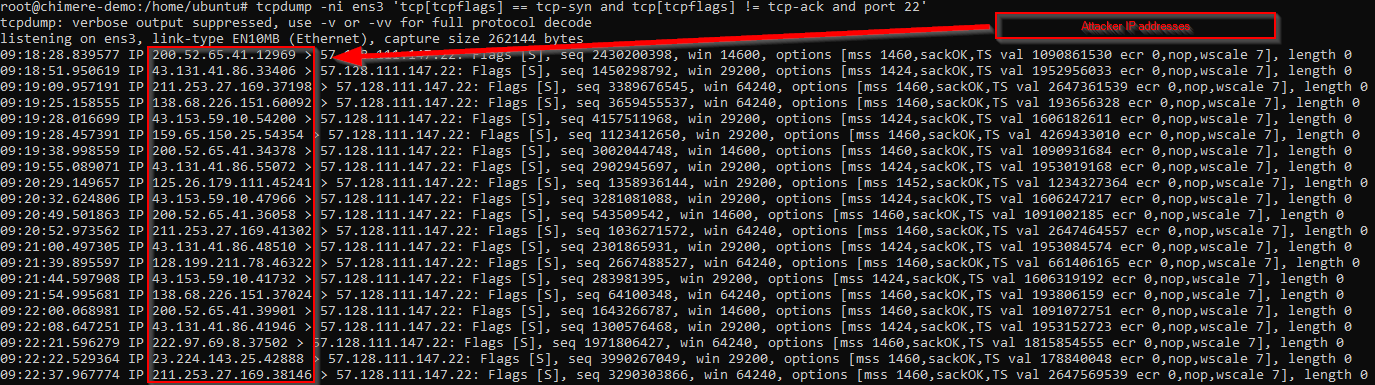
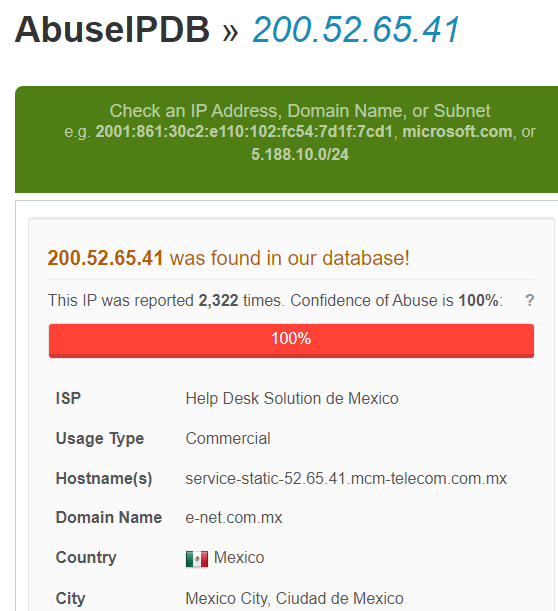
Who's knocking on our door? Let's take the very first identified address (200.52.65.41) and do a quick Google search. No doubt, the online service IPDB informs us that it is a Mexican IP address known for conducting malicious actions:
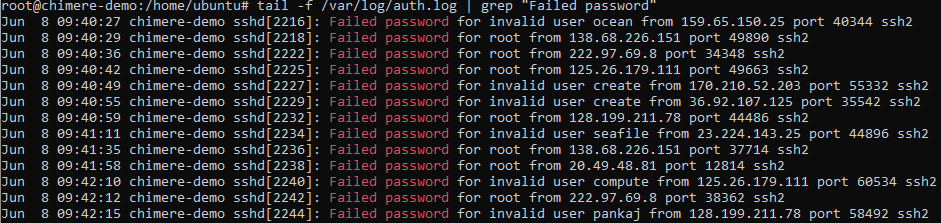
We can also verify that there are indeed attempts of attacks and authentication on our SSH service. To do so, simply search for failed authentication attempts in the logging using the following command:
tail -f /var/log/auth.log | grep "Failed password"
Result:
Let's see how to prevent these attacks by hiding our service on the Tor darknet.
Publishing the application on the darknet
The first thing to do is to install Tor on the machine to enable registering our service on the darknet:
apt install tor
Then, we verify that the Tor process is running properly:
systemctl status tor
Now, we will configure the machine to publish our SSH service on the darknet.
First, we identify the interfaces on which the service is listening:
netstat -lpa
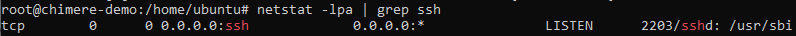
The service is listening on 0.0.0.0, which means it is also accessible from the loopback address 127.0.0.1. In other words, a program on our machine can locally contact the SSH service by initiating a connection to 127.0.0.1 port 22.
Let's use this information to configure the Tor process to point to 127.0.0.1 and port 22, making this service accessible via the darknet.
We edit the Tor configuration file /etc/tor/torrc and add the following lines:
HiddenServiceDir /var/lib/tor/ssh/
HiddenServicePort 22 127.0.0.1:22
The first line specifies to use the directory /var/lib/tor/ssh/ as the data directory for our service. This directory will contain the cryptographic key and the onion address of the service, which we will later use to connect to the SSH application through the Tor darknet.
The second line indicates to publish access to the final service at 127.0.0.1:22 through the darknet, also using port 22. The onion address must be associated with a port to access the service. Here, we specify the same port as the exposed service. This is not a problem because the port cannot be scanned by attackers without knowledge of the onion address of the service.
Let's restart the Tor service to apply the changes:
systemctl restart tor
Accessing the application through the darknet
Now that the service is published, we will access it.
The file /var/lib/tor/ssh/hostname contains the onion address of our service, which was generated during the registration process:
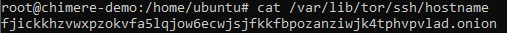
Let's copy this address, as it will be useful for accessing the service.
On our workstation, we will also install Tor. We are using a Linux workstation, but these steps can also be adapted for Windows and MacOS:
apt install tor
Once installed, the Tor process provides a local proxy listening on 127.0.0.1 and port 9050. Any SOCKS5 request sent to this address and port is routed to the Tor darknet.
Therefore, it is sufficient to specify the previously obtained onion address to connect to the service.
To facilitate the use of the SSH client through the Tor proxy, we use the program torsocks, and we execute the connection command to the service:
torsocks ssh ubuntu@fjickkhzvwxpzokvfa5lqjow6ecwjsjfkkfbpozanziwjk4tphvpvlad.onion
And now we are connected to the SSH service through Tor:
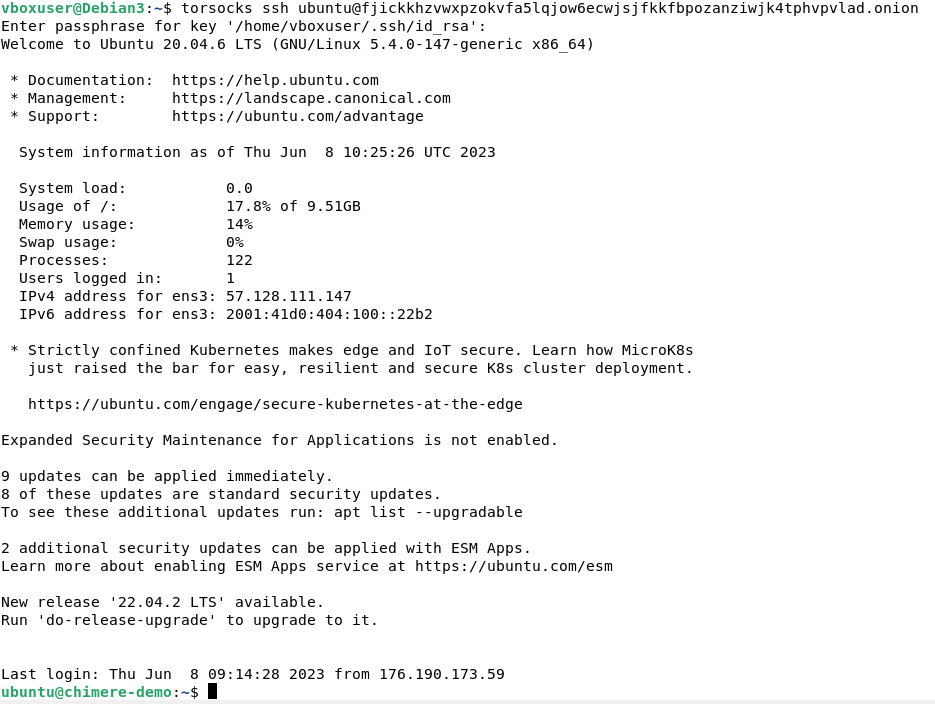
Now we will use this connection to disable the service's exposure on the internet and avoid being targeted by attacks.
Disabling service exposure
As we have seen earlier, the SSH service is listening on all interfaces and is therefore exposed on the internet. We want to limit its exposure to the loopback interface to allow the Tor process to access it, but not external clients.
There are several ways to achieve this. For example, we could add a firewall rule or simply modify the service's listening interface.
Let's focus on the second option.
We edit the SSH configuration file /etc/ssh/sshd_config, and then add the following line:
ListenAddress 127.0.0.1
Finally, we restart the SSH service to apply the changes:
systemctl restart sshd
If we try to connect directly to the service without going through the darknet, we do indeed receive a refusal.
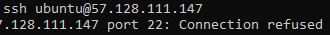
And now, what about the attacks?
Let's take a look at the logging file again. Are we still seeing authentication attempts from attackers?
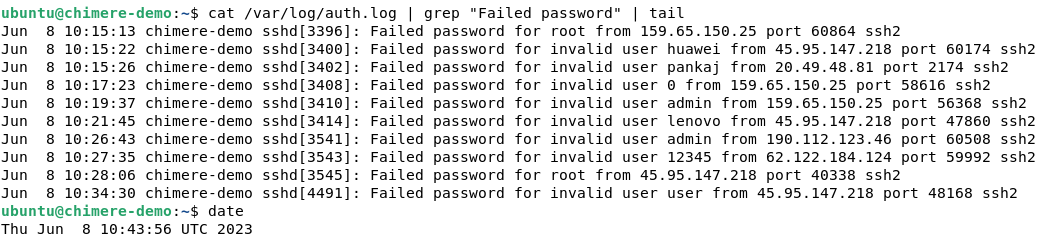
The authentication attempts have stopped since the service exposure was disabled. It has become undetectable, and only those who know the onion address (which is actually a cryptographic key) are able to negotiate a connection with the service, now hidden on the Tor darknet.
Generalizing the concealment of services
Of course, the Tor network is not suitable for widespread concealment of enterprise services.
It is cumbersome to automate the concealment of dozens or hundreds of services, require users to manipulate .onion addresses to access their services, or accept the network's low performance.
For all these reasons, we have designed the Chimere network: a private, user-friendly, high-performance darknet that allows centralized and on-premise management of user lists, services, and associated access rights. Chimere is also designed to enable all users to access hidden services using the programs they are accustomed to using on a daily basis.
To learn more about Chimere, feel free to visit our website, and sign up for the newsletter to stay updated on upcoming articles.
