Chimere Cyberstealth®
Zero Trust by design network access solution
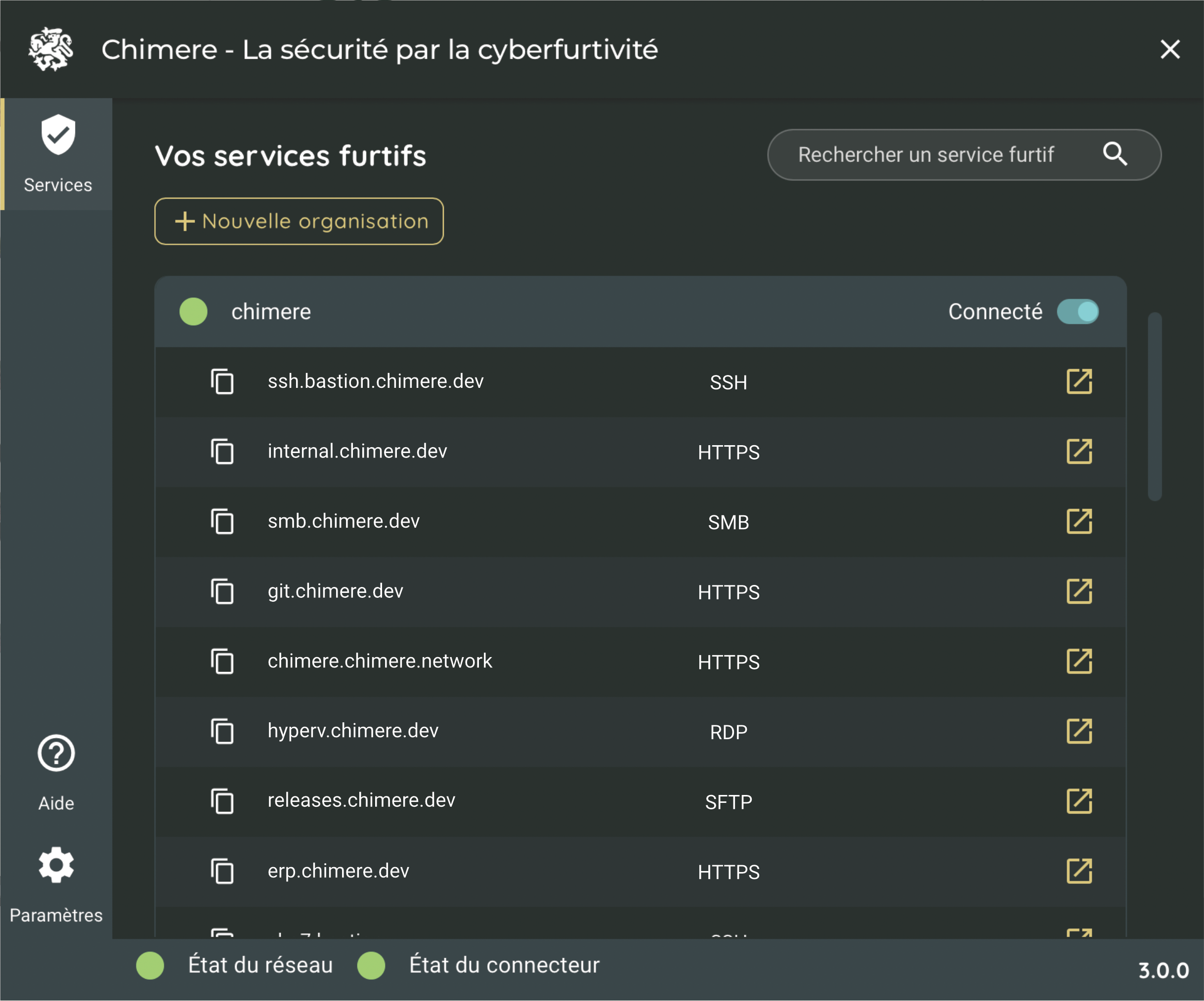
User Agent
This component allows the user to connect to the ZTNA infrastructure and the applications of their company.
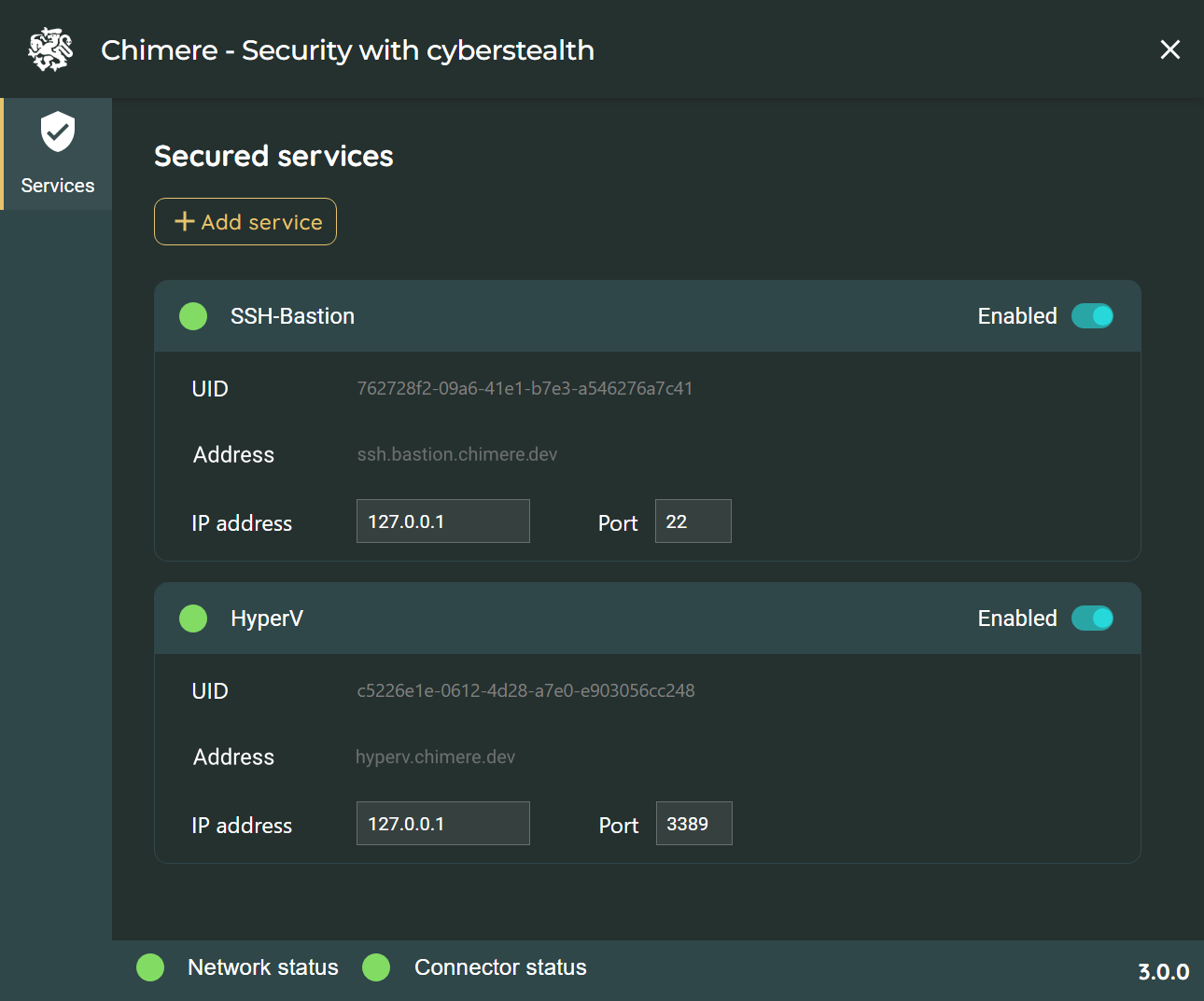
Transfer Agent
The transfer agent allows the connection and provision of services and applications to users.
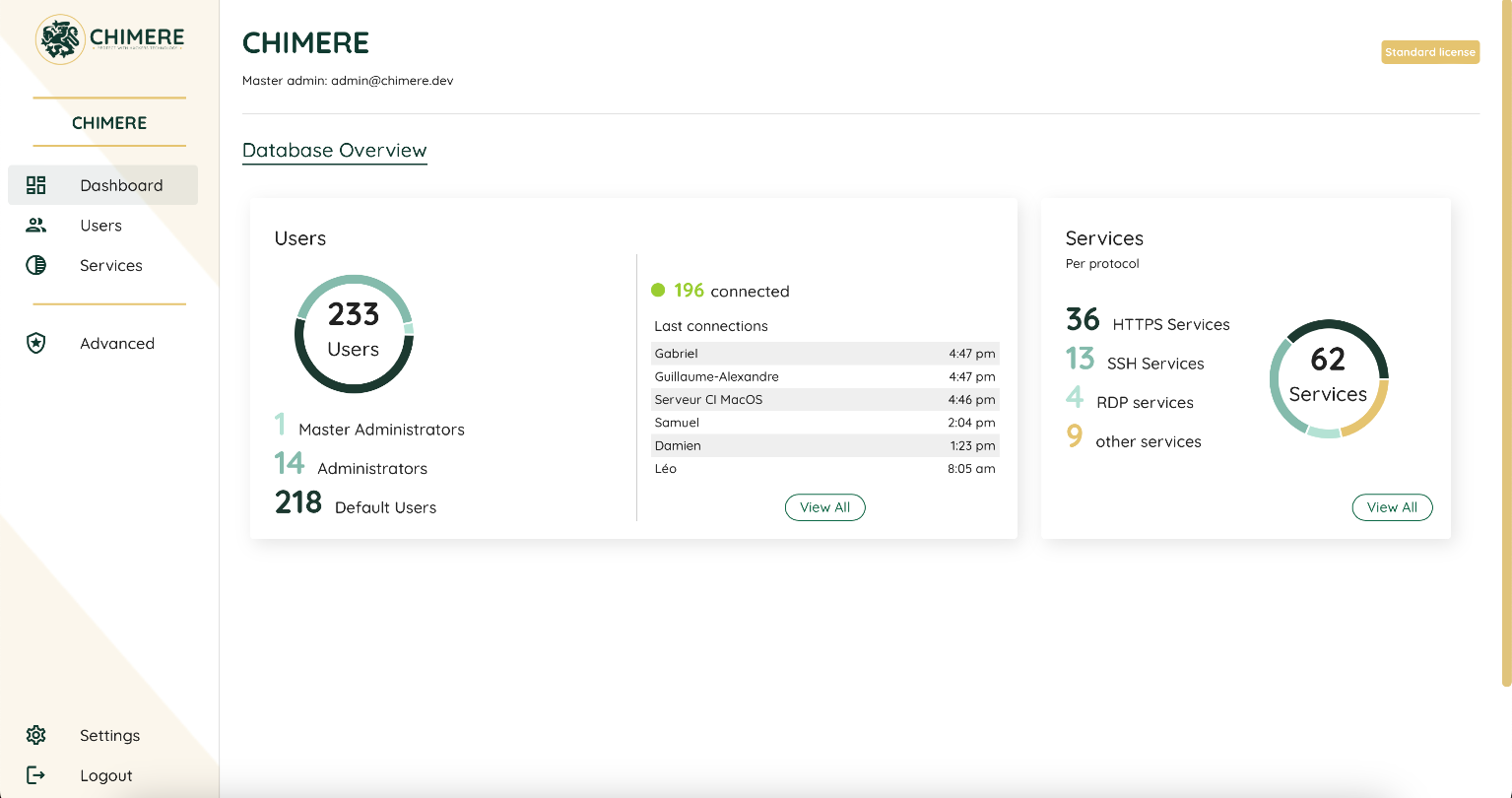
Chimere Manager
The administration console allows managing access rights, users, and secured applications.
Chimere Network
The network enables users and protected services to connect without trusting Chimere. The true Zero Trust.